Cis Controls Audit Assurance Program
Even though budgets increase and management pays more attention to the risks of data loss and system penetration data is still being lost and systems are still being penetrated. 10 In planning the portions of the audit which may be affected by the entitys CIS environment the auditor should obtain an understanding of the significance and complexity of the CIS.

The Cis 20 Organizational Controls Controls 17 20 Explained Secure Ops
Each of these 20.

Cis controls audit assurance program. Tuesday February 6 2018. CIS Controls 1 6 represent well known cybersecurity basics and focus on the fundamentals of securing the infrastructure and monitoring it regularly for changes including Configuration Management Vulnerability Assessment and Continuous Monitoring to know when a new critical vulnerability surfaces or an asset becomes exposed. This topic deserved a substantial treatment and resulted in the Implementation Groups discussed below.
This dashboard is used with the CIS Control Assessment Specification CAS to show organizations how to measure the controls supported by Tenablesc. Basic foundational and organizational. Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations around the globe.
Governance Foundation of a Security Program. Complete the form to get access to CIS Controls V71. In recent years it has become obvious that in the world of information security the offense is outperforming the defense.
Audit the CIS Controls v8 as documented by the Center for Internet Security CIS. Lack of visible transaction trails. The CIS Critical Security Controls comprises a set of 20 cyberdefense recommendations surrounding organizational security split into three distinct categories.
In particular many of you have asked for more help with prioritizing and phasing in the CIS Controls for your cybersecurity program. The CIS Controls security standard is a set of guidelines formerly known as the SANS Top 20 Critical Security Controls that gives your organization a reliable universally-recognized foundation for cybersecurity. Controls the auditor should obtain an understanding of the internal control structure sufficient to plan the audit and develop an effective audit approach.
Unlike the recommendations youll get from security vendors these controls are accepted and trusted as best practices that are used by a variety of brands. The CIS Controls structure. Focusing on the primary security and controls for protection of sensitive data intellectual property networks and responsibility and accountability for devices and information within the network CIS Controls audits aim to achieve the following.
Analysis of Audit Logs CIS Controls V7 Inventory and Control of Hardware Assets. At CIS we listen carefully to all of your feedback and ideas for the CIS Controls. For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed.
A CIS Controls Assessment provides risk reduction and protection against dangerous threat actors. The Center for Internet Security CIS officially launched CIS Controls v8 which was enhanced to keep up with evolving technology now including cloud and mobile technologies. Inventory and Control of Enterprise Assets SECTION 4.
SANS Analyst Program 2018 SANS Institute Sponsored by. While the CIS Controls AuditAssurance Program is not designed to provide assurance beyond the security program of an enterprise the controls are presented in a prioritized fashion to assist the enterprise in leveraging its potentially limited resources to. The CIS Controls AuditAssurance Program takes a high-level approach to providing assurance.
Ease of access to data and computer programs. To aid customers CIS produced a Control Assessment Specification CAS which provides a very detailed set of input metrics and other details about how to measure the compliance. CISOs IT security experts compliance auditors and more use the CIS Controls to leverage the expertise of the global IT community focus security resources based on proven best practices and organize an effective cybersecurity program according to Implementation Groups.
CIS Controls were created by IT and cybersecurity experts who wanted to compile global best security practices and prevent. AUDITING IN A COMPUTERIZED. Two types of internal control in CIS environment - General controls - Application Controls.
CIS Critical Security Controls for Effective Cyber Defense Version 61 August 31 2016 A Measurement Companion to the CIS Critical Security Controls Version 6 October 2015. CIS Controls IS AuditAssurance Program CIS Controls AuditAssurance Program In preparation for audits conducted using this IS auditassurance program two key documents are recommended reading. The CIS Critical Security Controls.
SecurityMetrics uses the latest CIS Controls version 8 to strengthen and protect your network against advanced threats. In 2008 the Information Assurance Directorate IAD of the National Security Agency was tasked with performing penetration testing and red team exercises against government. The CIS Critical Security Controls also have cross-compatibility andor directly map to a number of other compliance and security standards many of which are industry specificincluding NIST 800-53 PCI DSS FISMA and HIPAAmeaning organizations that must follow these regulations can use the CIS controls as an aid to compliance.
ENVIRONMENT Characteristics of CIS ack of visible transaction trails onsistency of Performance ase of Access to Data and Computer Programs oncentration of duties ystems generated transactions ulnerability of data and program storage media Internal Control in a CIS Environment General Controls These are controls which relate to the environment within which. CIS AuditAssurance Program Help Enterprises Navigate Risk. List 3 of characteristic audit CIS 1.
Information assurance auditors System implementers or administrators Network security engineers.
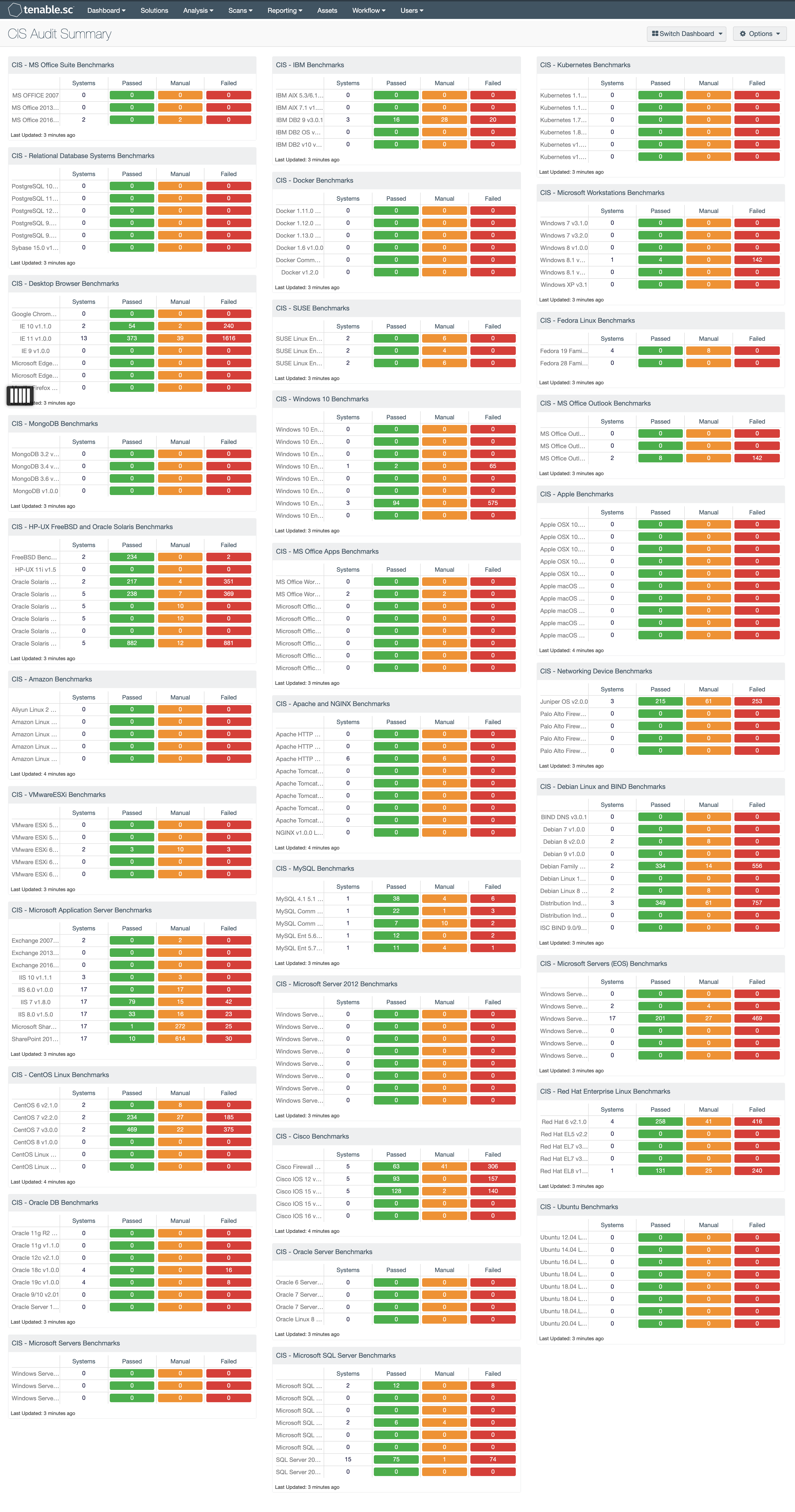
Cis Audit Summary Sc Dashboard Tenable

Cis Critical Security Controls
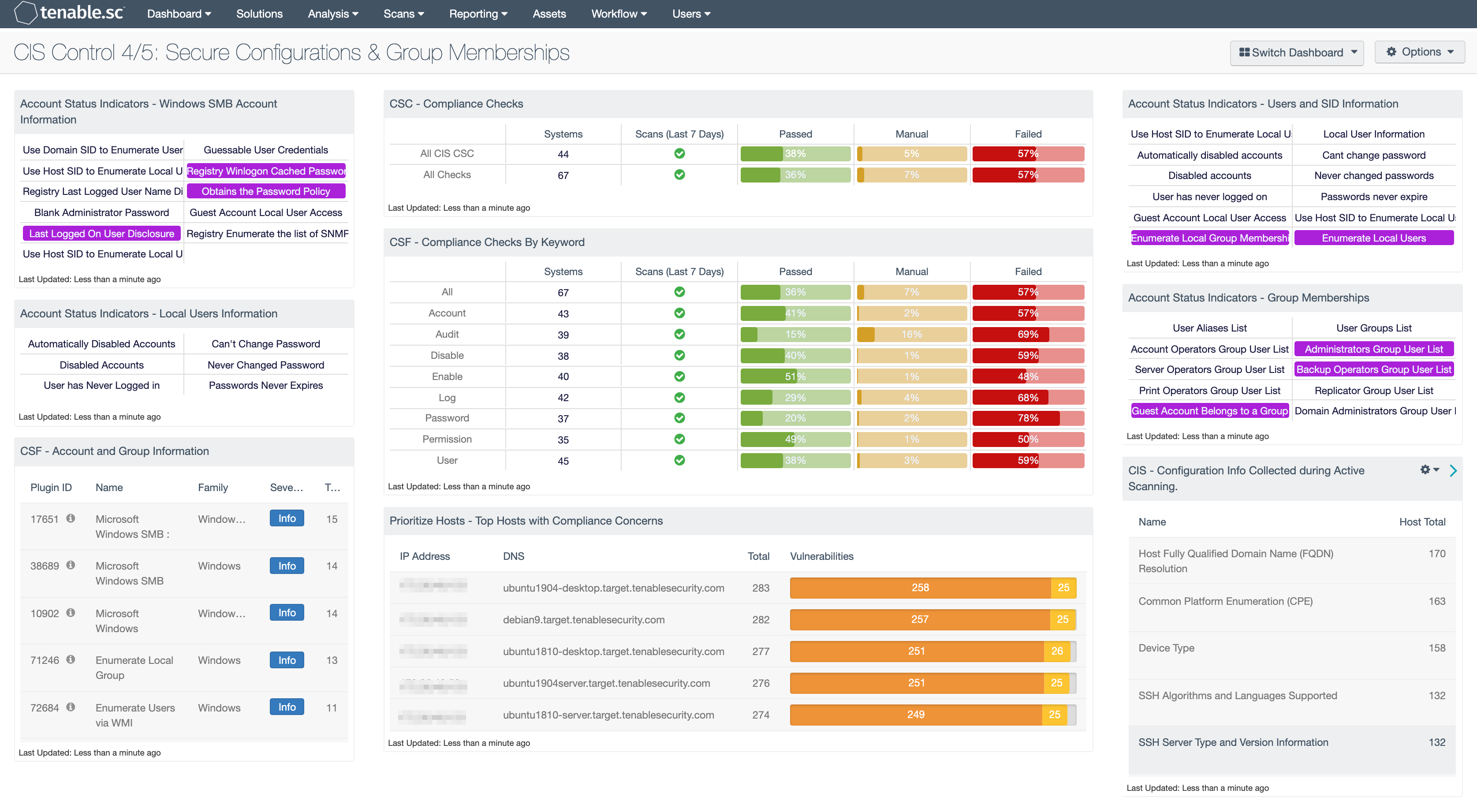
Cis Control 4 5 Secure Configurations Group Memberships Sc Dashboard Tenable
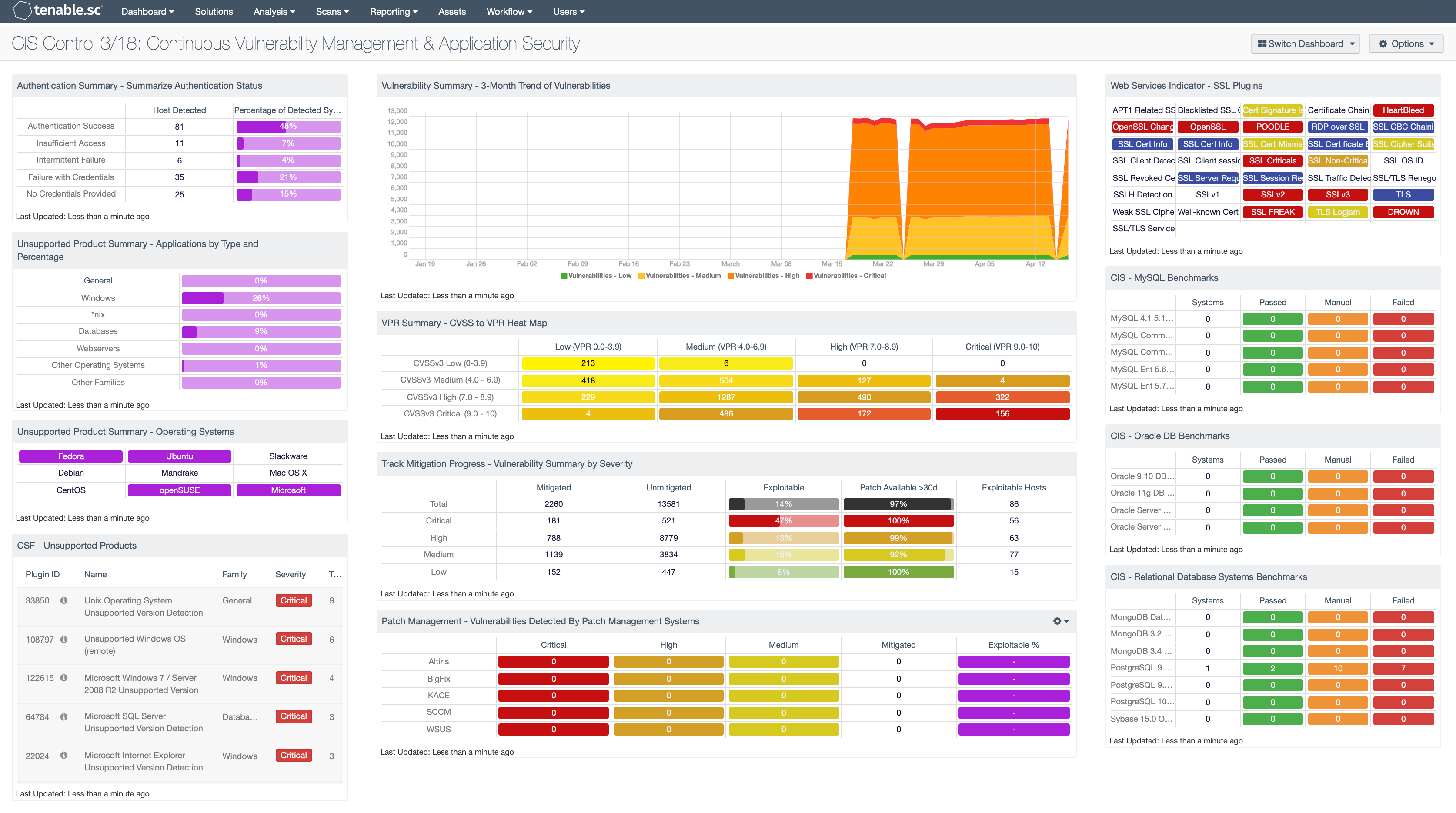
Cis Control 3 18 Continuous Vulnerability Management Application Security Sc Dashboard Tenable

What Are The Cis Controls For Effective Cyber Defense Upguard
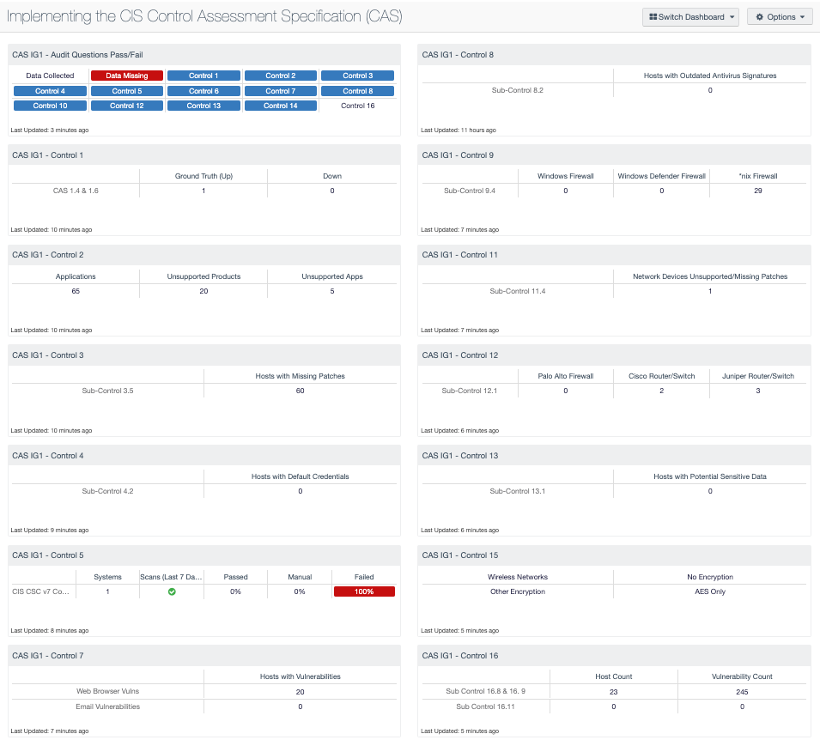
Implementing The Cis Control Assessment Specification Cas Sc Dashboard Tenable

12 Commonly Asked Questions About Cis Controls I S Partners
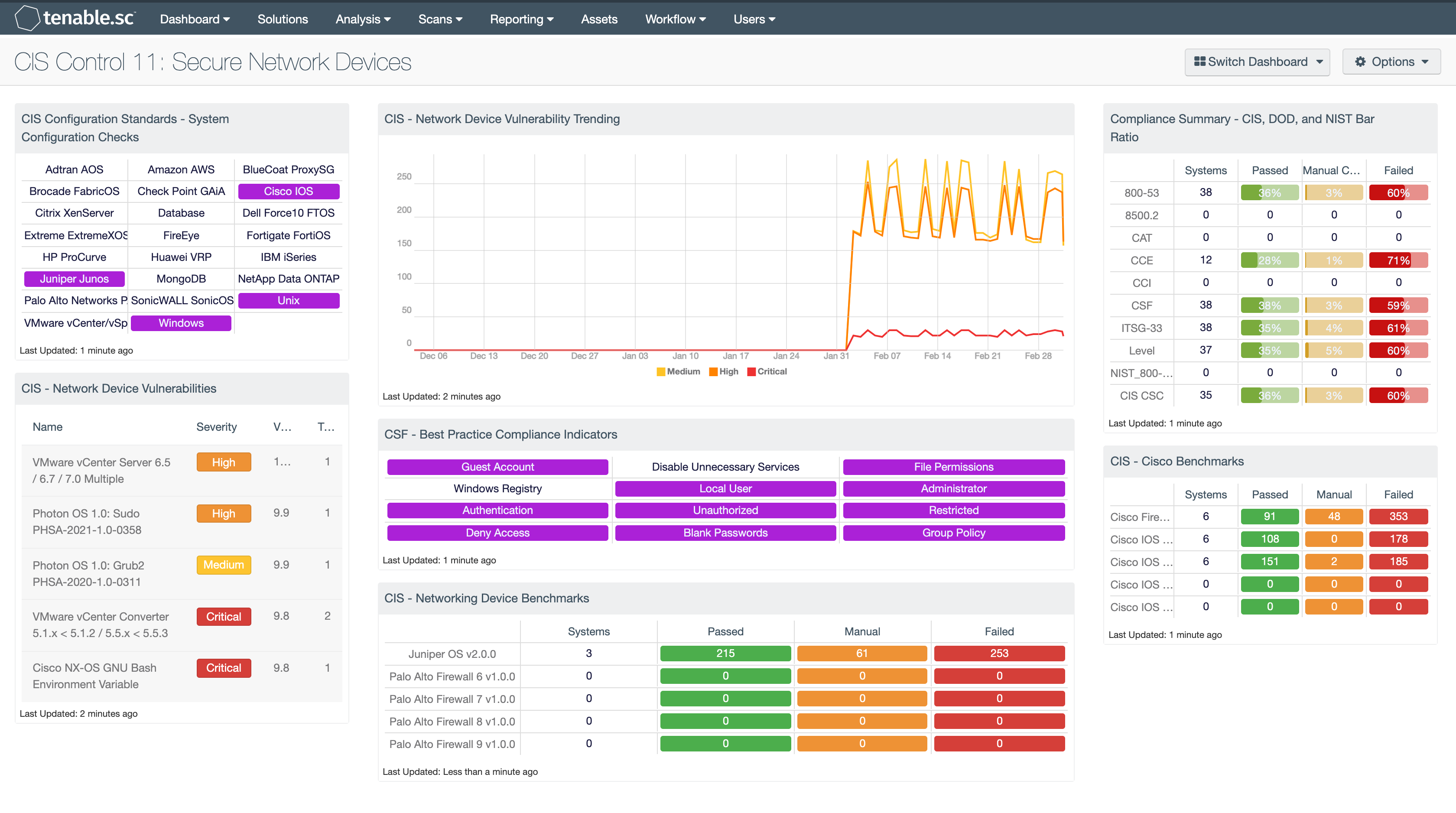
Cis Control 11 Secure Network Devices Sc Dashboard Tenable

The 18 Cis Critical Security Controls

The 18 Cis Critical Security Controls

Cis Control 3 Continuous Vulnerability Management

The 20 Critical Security Controls From Framework To Operational To Implementation Youtube

Prioritizing A Zero Trust Journey Using Cis Controls V8

The 18 Cis Critical Security Controls

Implementing The Cis Control Assessment Specification Cas Sc Report Template Tenable
Outsystems Compliance Outsystems

Cybersecurity Quarterly Summer 2021 By Cybersecurity Quarterly Issuu

Cis Critical Security Controls
Posting Komentar untuk "Cis Controls Audit Assurance Program"